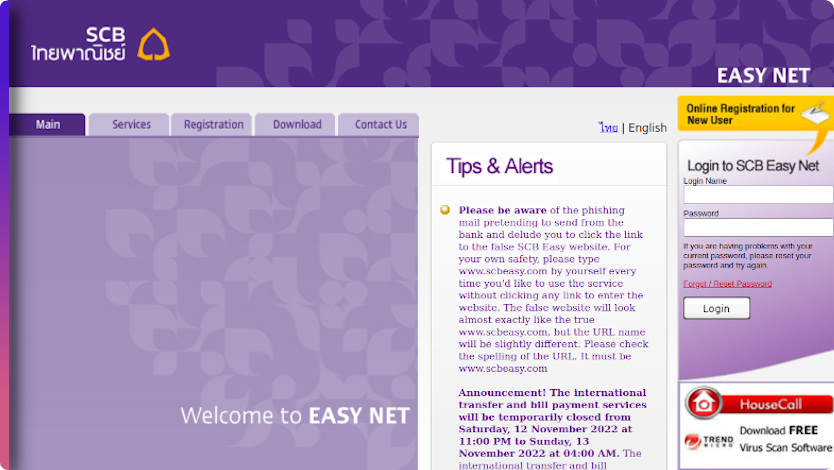
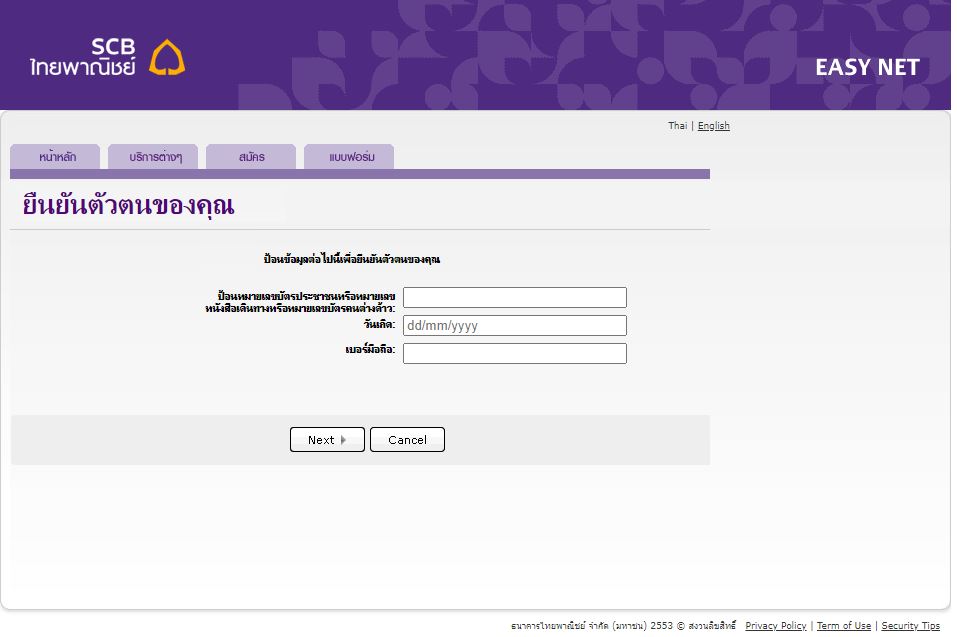
In the latest phishing exploit discovered by novoShield, attackers were able to host their phishing site by gaining access to a private Purdue Career Account and to upload their phishing site through it.
At the time of writing this, the phishing site is active, and both Chrome and Safari do not block it.
Sneaky sneaky
The attackers employ a couple of evasive techniques to make the phishing appear more legitimate to users, as well as to fool automated defences.
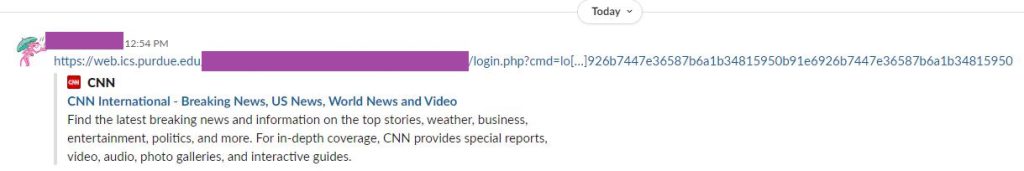
The first method is user agent-based redirecting: when browsed from a non-standard user agent (not Chrome/Safari, for example), the server redirects to another domain. This causes some apps, which use URL previews, to display the redirected (legitimate) web site’s content as preview, even though the link would otherwise lead to the phishing site.
This is how it looks on Slack:
And on Telegram:
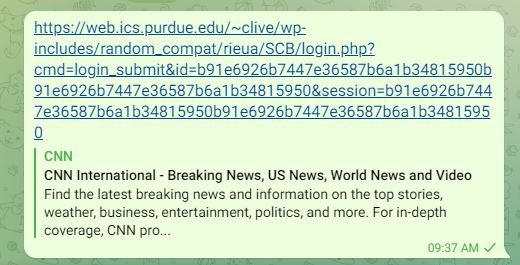
Additionally, if phishing detection systems do not make sure to change their user agent to a standard user agent, they will arrive to a different page than the phishing page and will not be able to detect the page as malicious.
The second method is hosting the site on a legitimate domain. Being hosted on a reputable domain often significantly reduces the likelihood of being flagged as phishing.
The third method is using unique ID parameters for different victims, causing each target to access a different URL. Two examples:
![]()
This common tactic is used in order to bypass blocklisting defenses. Any given ID will result in the user reaching the phishing page; so blocking a single (complete) URL is meaningless.
Additionally, as the phishing page is hosted on a legitimate domain, defenders cannot blocklist the entire domain without blocking access to legitimate web pages
The phish
The phishing site itself is composed of images copied directly from the target site and a login form asking for a username and password:
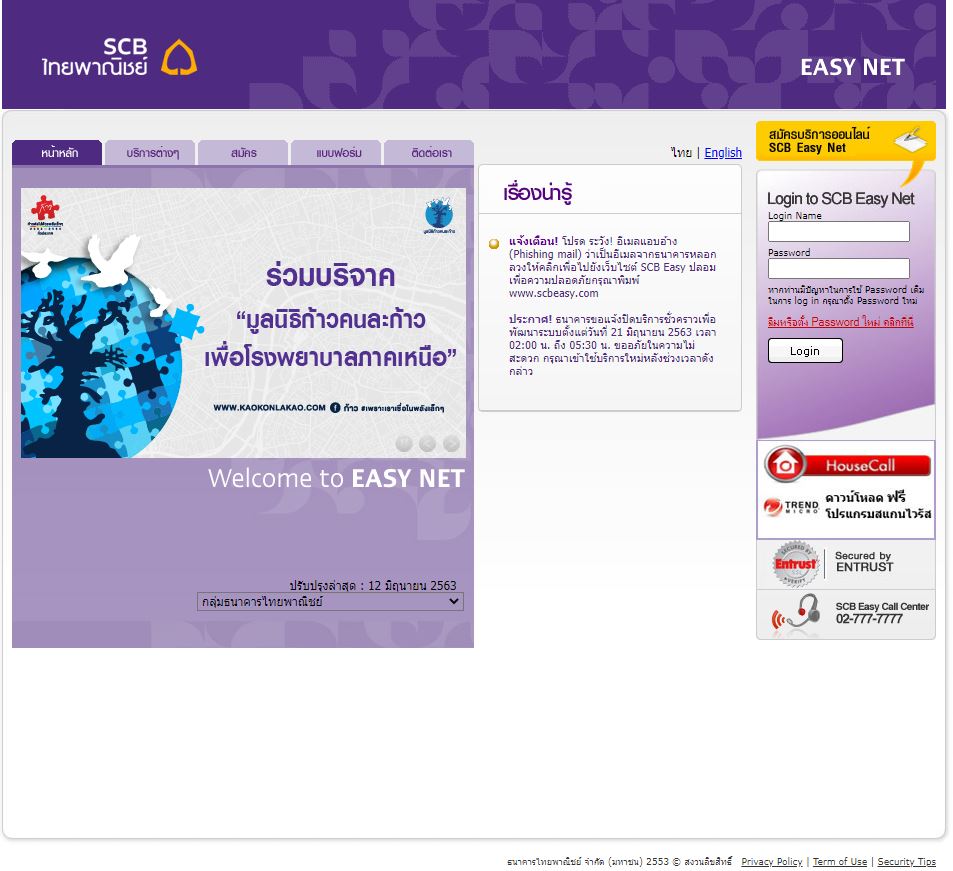
The site requests users to enter credentials twice, to avoid incorrect credentials due to typos.
Upon providing credentials, the attackers move to ask for additional information:
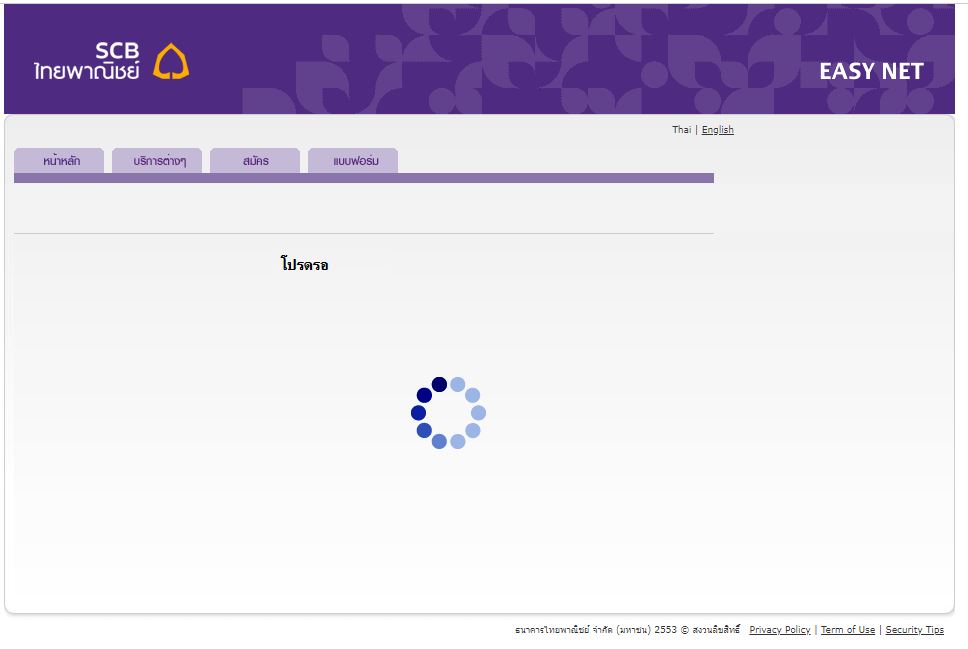
And finally, the attackers display a ‘loading animation’ page that never changes, likely to lead the victim into thinking that an error has occurred and to avoid raising suspicion:
Conclusion
Attackers continue to be creative by coming up with methods to make phishing attacks look more legitimate, thereby reducing the likelihood of being detected by defenses.
Even though the used techniques are relatively simple, combining them leads to an effective attack that is often missed by defensive systems and by the users themselves.
At novoShield, our team continuously researches new phishing methodologies, to keep up with the rapid pace that the attackers are setting.





